Earlier tonight a tweet caught my eye.
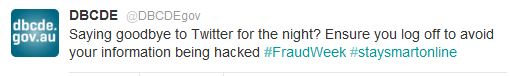
Incorrect security advice from a government department, who would have thought. You would think the Government could do better, but no. Apparently logging off will keep you safe. This isn’t the early 90s anymore an threats have grown beyond another user on the computer after you. Besides do people really share computer much these days anyway? Even if they do, an errant sibling or spouse is your least concern.
As part of fraud week I thought I would post something a little more useful than the Australian Government. While there are many security threats both online and offline the one I keep needing to educate users about is Phishing. Whereby criminals will impersonate a legitimate website in order to trick a user into supplying their username and password for the legitimate site.
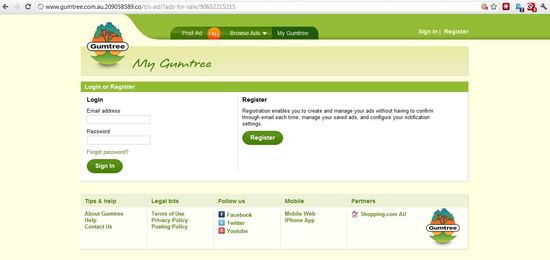
For example have a look at this website. (click the image)
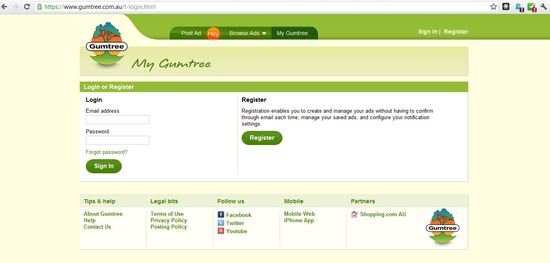
Now take a look at the second website (click the image)
Did you spot the difference? Unfortunately allot of people do fail to spot the difference and become victims of crime due to the theft of their credentials. This is because only one of these websites is real and the other a fake. If you happen to enter your username and password into the fake site then your credentials are in the hands of the criminals running the fake site; this process is called “Phishing”.
Here is the all important difference that users need to be taught to look for.

It’s in the URL, while both sites contain gumtree.com.au only one of those sites is actually gumtree.com.au while the fake site is actually a subdomain in disguise. Just because you see the name in the address bar it doesn’t mean you are at the correct site. In this case the criminal owns 209058589.co (the domain extension for Columbia) and you’re simply visiting a subdomain hosting the fake site.
One of the ways criminals trick users into going to the wrong site is by sending them an email pretending to be from the legitimate site but instead linking to the fake site. Users with HTML enabled are especially at risk because urls are much easier to hide inside of hyperlinks. For example http://www.microsoft.com links straight back to this article, but if placed in an official looking email pretending to be from Microsoft a user could be duped into thinking it’s a link to microsoft.com when it actually links elsewhere. This tactic combined with a good fake site and URL is enough to fool most users.
So as part of #FraudWeek teach some of the less tech savvy users how to spot the fakes. Just because you can spot them it doesn’t mean your friends and family can.
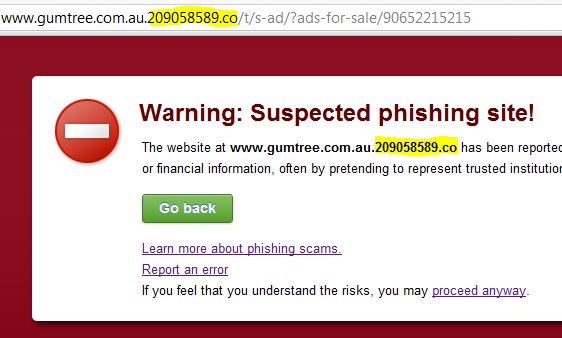 Google Chrome blocking access to a Phishing site.
Google Chrome blocking access to a Phishing site.
Fortunately most modern web-browsers have the ability to scare users away from Phishing sites, but they shouldn’t be solely relied upon as some Phishing sites do manage to escape detection. Therefore user education is the key.