Adblocking software has been in the news quite a bit recently due to their increasing popularity.
Guillermo Beltrà spends a lot of time surfing the web.
Yet like many avid Internet users, Mr. Beltrà hates the annoying pop-up advertisements that litter many websites. “It’s just very cumbersome,” he said.
So like a growing number of people, Mr. Beltrà, a Spaniard who works for a consumer protection organization in Brussels, decided to block them by downloading software for his desktop browser that removed any online advertising from his daily Internet activity.
While he acknowledged that advertising was often the primary source of income for many websites, Mr. Beltrà said he remained wary of how much data companies were collecting on his online activities. –Mark Scott, New York Times, Blog
I have long advocated the blocking of advertising network because while many user find advertisements “Annoying” there is a far more sinister side to advertising that marketers would rather you didn’t know about.
Unknown to many users is the fact that many advertising networks embed spyware that is designed to track you across the Internet with every website you visit. They do this by embedding trackers into the advertisement that your browser then loads whenever you vist Website X using Advertising Network Z. Now when you visit Website Y who just happens to be using Advertising Network Z you are instantly identified as the person who visited Website X earlier.
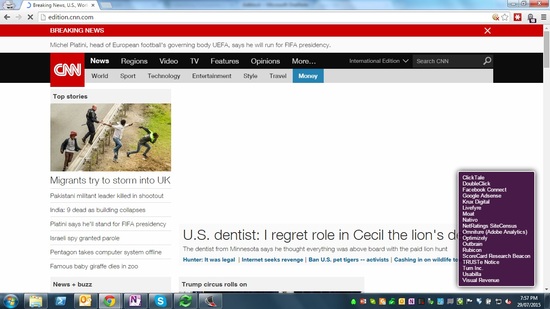
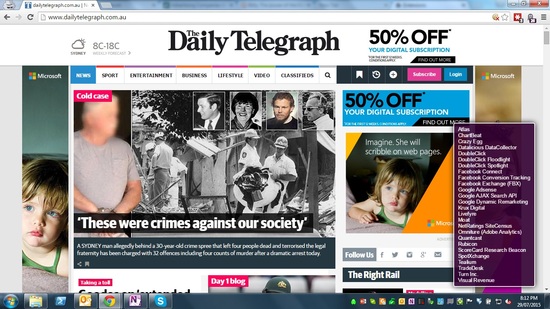
But the thing that surprises most people is just how many trackers an otherwise innocent website may harbour. Let’s take a quick sample; I am using the browser extension Ghostery to show detected trackers in the purple box bottom right. (Click Images to Enlarge them.)
So CNN has 18 Trackers and The Daily Telegraph has 26 Trackers setup to betray their readers privacy, and these are only the trackers that Ghostery is able to detect.
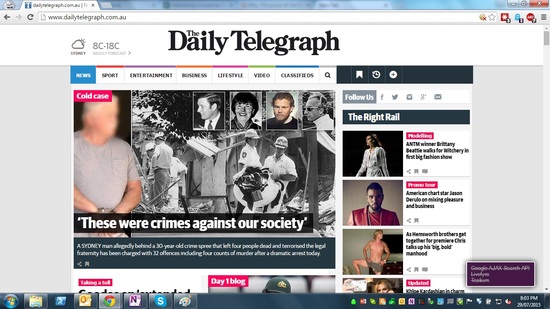
Let’s check the last site again with both trackers and advertisements blocked:
Now we can see that AdBlockPlus has removed 23 of the 26 trackers and all the advertisments. Ghostery has detected and blocked the three remaining trackers.
These are only two websites on the Internet that I have chosen to demo for no particular reason. There is nothing abnormal about the behaviour of these sites, it is now a common practice for website operators to install malware (spyware) into websites for commercial gain because there is a lot of money to be made in violating your privacy.
It wasn’t always like this. Advertising didn’t used to involve malicious action towards the end user. Although advertisements have always been annoying it is only over the course of the past decade that they have become a specific threat that users need to block by default.
Fortunately there is a way to block most of these trackers. I highly recommend everybody install AdBlock Plus and Ghostery into their browser. Both programs are free and both will block trackers. Ghostery in particular will give you an alarming insight into just how many trackers are being used to invade your privacy. I have been using both programs for years and would not consider browsing the Internet without either of them.